Introduction to DKIM
DKIM (DomainKeys Identified Mail) is a method to verify that the content of email messages remains trustworthy and unchanged from the moment they leave the initial mail server. This verification is achieved through a public/private key signing process. Domain owners add a DNS entry with the public DKIM key, which receivers use to verify the DKIM signature. On the sender's side, the server signs outgoing messages with the private key.
Here's how it works:
- When sending an outgoing message, the last server within the domain infrastructure checks its internal settings to see if the domain in the "From:" header is included in its "signing table." If not, the process stops.
- A new header, "DKIM-Signature," is added to the mail message using the private key on the message content.
- From here on, the message content cannot be modified without invalidating the DKIM header.
- Upon reception, the receiving server makes a TXT DNS query to retrieve the public key used in the DKIM-Signature field.
- The DKIM header check result helps determine if a message is fraudulent or trustworthy.
Similar to an SSL certificate, a private key is generated on the server to sign all outgoing emails, while a public key is added to the domain DNS zone as a TXT record for signature verification.
Update System
First, update your server and ensure you're in a screen session:
screen -U -S opendkim-screen
yum update -y
Enabling EPEL Repository
OpenDKIM is available in the EPEL repository, so enable it:
wget -P /tmp http://mirror.pnl.gov/epel/6/i386/epel-release-6-8.noarch.rpm
rpm -Uvh /tmp/epel-release-6-8.noarch.rpm
rm -f /tmp/epel-release-6-8.noarch.rpm
Installing OpenDKIM
Install OpenDKIM using yum:
OpenDKIM Configuration
Before making any changes, back up the main configuration file:
cp /etc/opendkim.conf{,.orig}
nano /etc/opendkim.conf
Add or edit the following lines:
AutoRestart Yes
AutoRestartRate 10/1h
LogWhy Yes
Syslog Yes
SyslogSuccess Yes
Mode sv
Canonicalization relaxed/simple
ExternalIgnoreList refile:/etc/opendkim/TrustedHosts
InternalHosts refile:/etc/opendkim/TrustedHosts
KeyTable refile:/etc/opendkim/KeyTable
SigningTable refile:/etc/opendkim/SigningTable
SignatureAlgorithm rsa-sha256
Socket inet:8891@localhost
PidFile /var/run/opendkim/opendkim.pid
UMask 022
UserID opendkim:opendkim
TemporaryDirectory /var/tmp
Setting Up Public/Private Keys
Generate keys for your domain:
mkdir /etc/opendkim/keys/your_domain.com
opendkim-genkey -D /etc/opendkim/keys/your_domain.com/ -d your_domain.com -s default
chown -R opendkim: /etc/opendkim/keys/your_domain.com
mv /etc/opendkim/keys/your_domain.com/default.private /etc/opendkim/keys/your_domain.com/default
Add your domain to OpenDKIM's key table:
nano /etc/opendkim/KeyTable
Add the following record:
default._domainkey.your_domain.com your_domain.com:default:/etc/opendkim/keys/your_domain.com/default
Edit the signing table:
nano /etc/opendkim/SigningTable
Add this record:
*`@your_domain`.com default._domainkey.your_domain.com
Edit the trusted hosts:
nano /etc/opendkim/TrustedHosts
Add your domain and hostname:
127.0.0.1
your_domain.com
your_servers_hostname.com
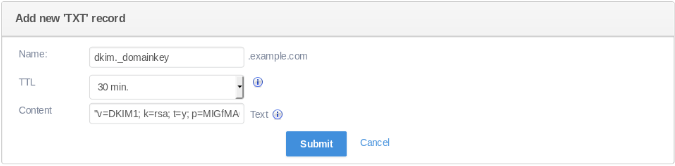
Adding the Public Key to The Domain's DNS Records
Setting up the DNS record for DKIM depends on how you manage DNS. Some registrars do not allow the creation of raw TXT records with specific subdomains, which is necessary for DKIM. If your registrar does not support this, you will need to transfer your domain to one that does, or use a DNS management system that provides this capability.
To find your public key, use the following command:
cat /etc/opendkim/keys/your_domain.com/default.txt
Here is how it looks on our DNS management system:
Integration with Mail Servers
Postfix
Add the following lines to /etc/postfix/main.cf:
nano /etc/postfix/main.cf
Add:
smtpd_milters = inet:127.0.0.1:8891
non_smtpd_milters = $smtpd_milters
milter_default_action = accept
milter_protocol = 2
Start OpenDKIM and restart Postfix:
service opendkim start
chkconfig opendkim on
service postfix restart
Exim
Edit /etc/exim/exim.conf:
Add to the remote_smtp transport:
remote_smtp:
driver = smtp
dkim_domain = $sender_address_domain
dkim_selector = default
dkim_private_key = ${if exists{/etc/opendkim/keys/$sender_address_domain/default}{/etc/opendkim/keys/$sender_address_domain/default}{0}}
dkim_canon = relaxed
dkim_strict = 0
Restart Exim and OpenDKIM:
service opendkim start
chkconfig opendkim on
service exim restart
Testing
Allow time for DNS changes to propagate. Use a service like Mail Tester to verify your DKIM setup.
By following these steps, you can set up DKIM to enhance the security and trustworthiness of your email communications.